The Security Landscape
Every program is a potential target. Hackers will try to find security vulnerabilities in your applications or servers. Attackers will try to use these vulnerabilities to steal secrets, corrupt programs and data, and gain control of computer systems and networks. Your customers' property and your reputation are at stake. Security is not something than can be added to software as an afterthought, any more than a shed made out of cardboard can be made secure by adding a padlock to the door. You must identify the nature of the threat to your software and incorporate secure coding practices throughout the planning and development of your product. This article explains the nature of the threat. Other articles in this document describe specific types of vulnerabilities and give guidance on how to avoid them.
Contents:
Hackers, Crackers, and Attackers
The Threat Is Serious and Getting Worse
Types of Attacks
No Platform is Immune
Hackers, Crackers, and Attackers
Contrary to the usage by most news media, within the computer industry the term hacker refers to an expert programmer—one who enjoys learning about the intricacies of code or an operating system. In general, hackers are not malicious. When most hackers find security vulnerabilities in code, they inform the company or organization that's responsible for the code so that they can fix the problem. Some hackers—especially if they feel their warnings are being ignored—publish the vulnerabilities or even devise and publish exploits (code that takes advantage of the vulnerability). The malicious individuals who break into programs and systems in order to do damage or to steal something are referred to as crackers or attackers. Most attackers are not highly skilled, but take advantage of published exploit code and known techniques to do their damage. People (usually, though not always, young men) who use published code (scripts) to attack software and computer systems are sometimes called script kiddies.
Attackers may be motivated by a desire to steal money, identities, and other secrets for personal gain; corporate secrets for their employer’s or their own use; or state secrets for use by hostile governments or terrorist organizations. Some crackers break into applications or operating systems just to show that they can do it—nevertheless, they can cause considerable damage. Because attacks can be automated and replicated, any weakness, no matter how slight, can be exploited.
In a 2005 survey of over 800 software companies by CSO magazine (in cooperation with the U.S. Secret Service and the CERT Coordination Center), 37% of respondents said that hackers posed the greatest cyber security threat and 23% said current or former employees were the greatest threat. (One in five (21%) of the companies surveyed weren't sure who was the greatest threat, and the remainder cited such sources as foreign terrorists and competitors.)
The large number of insiders who are attacking systems is of importance to security design because, whereas malicious hackers and script kiddies are most likely to rely on remote access to computers to do their dirty work, insiders might have physical access to the computer being attacked. Your software must be resistant to both attacks over a network and attacks by people sitting at the computer keyboard—you cannot rely on firewalls and server passwords to protect you.
The Threat Is Serious and Getting Worse
Keeping in mind that the reputation of a software company can be ruined by a single well-publicized exploit against one of its products, it's sobering to note that, whereas 171 vulnerabilities were reported to the CERT Coordination Center (CERT/CC) in all of 1995, some 2,874 vulnerabilities were reported in the first half of 2005 alone. How does that relate to the number of actual attacks? CERT/CC states: "Given the widespread use of automated attack tools, attacks against Internet-connected systems have become so commonplace that counts of the number of incidents reported provide little information with regard to assessing the scope and impact of attacks. Therefore, as of 2004, we will no longer publish the number of incidents reported." (http://www.cert.org/stats/cert_stats.html) In other words, attacks are now so frequent, it's no longer practical to count them!
In January 2004, the MyDoom email virus spread so fast it caused some mail servers to shut down; at its peak, 20% to 30% of all emails over the Internet were generated by the virus. Lost productivity and technical support expenses were estimated at $250 million. In March 2005, Chinese police announced that they'd arrested a man accused of hacking into 100,000 computers, 40,000 of which were outside of China. In June 2005, attackers broke into a credit card database containing information on over 40 million credit card accounts. In April 2005, the unencrypted financial and medical records of nearly 185,000 current and former patients of a California medical group were compromised when two computers were stolen from their offices.
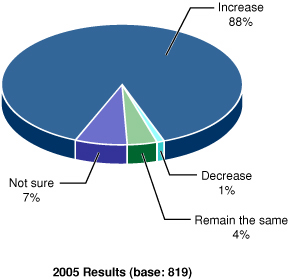
The situation does not seem to be getting better, either. In the survey by CSO magazine, 88% of respondents expected the prevalence of electronic crime to increase in 2005 relative to 2004 (Figure 1).
From 2005 E-Crime Watch Survey Summary of Findings, CSO magazine (CXO Media Inc.), in cooperation with the U.S. Secret Service and the CERT Coordination Center.
Respondents to the survey reported a mean of 86 network, system, or data intrusions or electronic crimes in 2004, ranging from none to over 250 for individual companies, counting each worm or virus as a single crime. The number of individual machines affected was much higher. Economic consequences reported in the survey varied widely, from none to over $10 million. The total monetary loss reported for 2004 by respondents to the survey was $150 million. These numbers reflect only direct attacks on the companies surveyed; adding in widespread losses such as those due to the MyDoom virus would inflate these numbers considerably.
Types of Attacks
Table 1 shows the answers to the CSO magazine survey question "Which of the following electronic crimes were committed against your organization in 2004?" Both electronic and social engineering attacks are common and increasing. (A social engineering attack is one in which a user is tricked into giving up secrets or into giving access to a computer to an attacker.) You should try to make your software resistant to cracking and your UI and customer education should aim to minimize the success of social engineering attacks.
Type | Percentage |
|---|---|
Virus or other malicious code | 82% |
Spyware | 61% |
Phishing | 57% |
Illegal generation of spam email | 48% |
Unauthorized access to information, systems, or networks | 43% |
Denial of service attacks | 32% |
Rogue wireless access point | 21% |
Exposure of private or sensitive information | 19% |
Fraud | 19% |
Identity theft | 17% |
Password sniffing | 16% |
Theft of intellectual property | 14% |
Zombie machines on organization's network | 13% |
Theft of other (proprietary) info | 12% |
Sabotage | 11% |
Website defacement | 9% |
Extortion | 2% |
Other | 4% |
Don't know/not sure | 3% |
No Platform is Immune
So far, Mac OS X has not fallen prey to any major, automated attack like the MyDoom virus. There are several reasons for this. One is that Mac OS X is based on open source software such as BSD; many hackers have searched this software over the years looking for security vulnerabilities, so that not many vulnerabilities remain. Another is that the default installation of Mac OS X turns off all networking services that might be used to exploit vulnerabilities. Also, the email and internet clients used most commonly on Mac OS X do not have privileged access to the operating system and are less vulnerable to attack than those used on some other common operating systems. Finally, Apple has an active program of reviewing the operating system and applications for security vulnerabilities and issues downloadable security updates frequently.
iPhone OS is based on Mac OS X and shares many of its security characteristics. In addition, it is inherently more secure than even Mac OS X because only one application can run at a time and each application is restricted in the files and system resources it can access.
That's the good news. The bad news is that open source code, all operating systems—including Mac OS X and iPhone OS—and applications that run on all operating systems are constantly under attack. Hackers discover vulnerabilities and publish exploit code. Criminals and script kiddies attack vulnerable systems. For example, recent security vulnerabilities in a variety of applications and operating systems include the following:
A buffer overflow vulnerability in a free multimedia player allowed a remote attacker to execute arbitrary code by sending a carefully crafted MPEG stream.
Flaws in decoding tiff images in open source code could permit the execution of arbitrary code.
Under some circumstances, the credentials used by a mail server to authenticate a user could be reused for a small time period, allowing an attacker to authenticate as the user.
Failure to validate input by a web calendar application allowed a remote attacker to execute arbitrary code by sending a crafted URL.
A vulnerability in a popular browser enabled an attacker to create an image on a web site that, when clicked by the user, would open a file or run code on the user’s machine.
[The following CVE numbers correspond to the numbers in the preceding list of vulnerabilities and refer to the Common Vulnerabilities and Exposures dictionary (http://www.cve.mitre.org/). You can run an Internet search on the CVE number to read details about the vulnerability:
1CVE-2006-1664 2CVE-2004-0803 3CVE-2004-1088 4CVE-2006-2261 5CVE-2006-1942]
This small sample illustrates that many vulnerabilities have been found on a variety of systems that, if exploited, could have resulted in loss of data, allowing an attacker to steal secrets, or enabling an attacker to run code on someone else's computer. A large-scale, widespread attack is not needed to cause monetary and other damages—a single break-in is sufficient if the system broken into contains valuable information. Although major attacks of viruses or worms get a lot of attention from the media, the destruction or compromising of data on a single computer is what matters to the average user. Because Apple Computer understands this principle, it takes every security vulnerability seriously and works to correct known problems quickly. For your users' sake and for the sake of your company's reputation, you should do the same.
If every Macintosh and iPhone OS developer follows the advice in this document and other books on electronic security, and if each Macintosh owner takes common-sense precautions such as using strong passwords and encrypting sensitive data, then Mac OS X and iPhone OS will maintain their reputations for being safe, reliable operating systems and your company's products will benefit from being associated with Mac OS X or iPhone OS.
© 2008 Apple Inc. All Rights Reserved. (Last updated: 2008-05-23)